How BIP39 Mnemonic Generators Work
Introduction to Ultimate Bip39 Mnemonic Generator Guide
Understanding how BIP39 mnemonic generators work is like lifting the hood on the engine of your crypto wallet. These generators take complex, high-entropy numbers and convert them into readable, memorizable word sequences from a standardized list called the BIP39 word list. Let’s go behind the curtain of how these tools function, what’s happening mathematically, and why this process is key to almost every wallet in the crypto world.
Definition of a BIP39 Mnemonic Generator
A BIP39 mnemonic generator is a software tool—online or offline—that helps you create a mnemonic seed phrase made up of 12, 18, or 24 words. These words aren’t just picked at random; they’re chosen based on a calculated entropy source, translated using a predefined BIP39 word list of 2048 words.
These generators follow the BIP39 specification line by line, ensuring that each word has a place and meaning. When used correctly, the phrase generated can be used to regenerate the exact same private keys, wallet addresses, and funds across multiple BIP39-compatible wallets.
Some popular versions include:
-
bip39 mnemonic generator online
-
bip39 mnemonic generator free
-
bip39 mnemonic generator GitHub tools
-
bip39 mnemonic generator Python scripts
You’ll find that these come in different formats: from clean, browser-based interfaces to hardcore command-line tools for crypto veterans.
How to Generate Mnemonics Using BIP39 Mnemonic Generator Online
If you’re looking for a fast and accessible way to create a seed phrase, an online bip39 mnemonic generator might be your go-to. But don’t rush into it—here’s how it works and what you should be cautious of.
Step-by-Step: Using a BIP39 Mnemonic Generator Online
-
Visit a Trusted Site: One of the safest options is Ian Coleman’s bip39 mnemonic generator GitHub-hosted tool. Download it and run it offline for max safety.
-
Select Entropy Strength: Choose between 128-bit (12 words) or 256-bit (24 words).
-
Click Generate: The tool will output a mnemonic phrase, a seed, and the derived private/public keys.
-
Backup Immediately: Save the mnemonic phrase somewhere offline—paper, metal plate, or air-gapped storage.
-
Test It (Optional): Use a watch-only wallet to see if the phrase is generating valid addresses. Never input this into unknown wallets.
Important: Never use online generators with real funds unless you trust the environment and have taken steps to secure it. Hackers love targeting browsers.
What is the BIP39 Word List?
The BIP39 word list consists of 2048 unique English words, carefully chosen to avoid ambiguity. You won’t find homophones like “their” and “there” or similarly spelled words that might get confused.
Each word has a binary index that corresponds to part of the entropy sequence. Here’s a taste of what the list includes:
-
abandon
-
ability
-
able
-
about
-
above
-
absent
-
absorb
-
abstract
And so on. Each mnemonic is built by slicing entropy into 11-bit sections and matching them to the corresponding word in this list.
You can find the full list in any bip39 mnemonic generator GitHub repo or on the official Bitcoin.org specs.
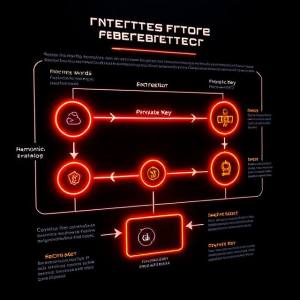
How Is Entropy Converted to Mnemonics?
This is where the magic happens.
-
Entropy Generation: First, a random string of bits (like 128 or 256) is created. This is your cryptographic randomness.
-
Checksum Addition: A checksum (part of the SHA256 hash of entropy) is added to increase integrity.
-
Bit Grouping: The combined string is divided into 11-bit chunks.
-
Word Mapping: Each chunk is mapped to a word from the BIP39 word list.
-
Mnemonic Phrase: Voilà! A readable seed phrase that represents your private key structure.
This system ensures your phrase is not only unique but also reversible into the original entropy by compatible wallets.
Understanding the BIP39 Mnemonic Code Structure
The BIP39 mnemonic code is deterministic. This means if you use the same entropy and BIP39 word list, you will always get the same mnemonic phrase. It also means that a phrase like:
isn’t just a random collection of words. It’s a mathematical representation of a private key, address path, and HD wallet structure.
From that phrase, tools can generate:
-
Master private key
-
Public keys
-
Derived addresses (using derivation paths like m/44’/0’/0’/0)
That’s why you must never share or lose your phrase. It’s everything.
From Private Key to Recovery Phrase — Is It Possible?
Now, let’s address the elephant in the room. You have a private key. Can you work backward and somehow get your original recovery phrase?
Can You Convert a Private Key Back to a Mnemonic Phrase?
Short answer: No, and here’s why.
A mnemonic phrase is derived from entropy, and from that entropy, you derive the private key. But going from private key to recovery phrase skips that middle step. And due to the cryptographic processes (including one-way hash functions), there’s no mathematical way to reverse it without knowing the original entropy.
This is by design. If it were reversible, your wallet security would be compromised. So unless you’re a quantum computer (and even then), it’s practically impossible.
BIP39 Mnemonic to Private Key: The One-Way Street Explained
Mnemonic ➜ Entropy ➜ Seed ➜ Master Private Key ➜ Wallet Keys
This is the only supported direction. Trying to reverse from private key to seed or private key to mnemonic is like trying to turn ashes back into firewood. It’s theoretically conceivable in some alternate physics universe—but not in ours.
Reverse Engineering the Process: Why It’s Nearly Impossible
Even if you have a valid private key, trying to reconstruct the exact entropy and checksum combination used in BIP39 is equivalent to brute-forcing over 2^128 combinations. That’s more than the number of atoms in the universe.
Plus, you’d have to:
-
Guess the derivation path
-
Rebuild the binary entropy
-
Validate against BIP39 checksum
All without knowing anything about the original setup. So yeah—good luck with that.
Security Risks Involved in Backwards Conversion
Here’s the kicker: if any tool claims to convert private keys to recovery phrases—run.
These are usually:
-
Malware-infected scam sites
-
Honeypots designed to steal your keys
-
Tools that output random phrases with zero correlation
Always stick to open-source, verifiable tools.