DeFi Asset Recovery: Navigating the Unforgiving Landscape of Decentralized Finance
DeFi Asset Recovery: Decentralized Finance (DeFi) offers unparalleled freedom, enabling users to lend, borrow, and trade without intermediaries. However, this permissionless environment comes with a significant trade-off: the absolute responsibility for security rests solely with the user. Unlike centralized exchanges, there is no customer support hotline for a mistaken transaction or a smart contract exploit. The immutable nature of blockchain means transactions are permanent.
Losing assets in DeFi—whether through user error, a malicious smart contract, or a sophisticated hack—can feel catastrophic. While recovery is notoriously difficult and never guaranteed, understanding the available avenues and acting swiftly can, in rare cases, lead to a positive outcome. This guide provides a clear, professional framework for navigating the possibility of DeFi asset recovery.
The Core Challenge: Why DeFi Recovery is So Hard
The very principles that make DeFi powerful—decentralization, immutability, and pseudonymity—make recovery exceptionally challenging.
-
No Central Authority: There is no company to call to reverse a transaction or freeze assets.
-
Irreversible Transactions: Once a transaction is confirmed on the blockchain, it cannot be undone.
-
Pseudonymous Actors: Scammers and hackers operate under wallet addresses, not real-world identities.
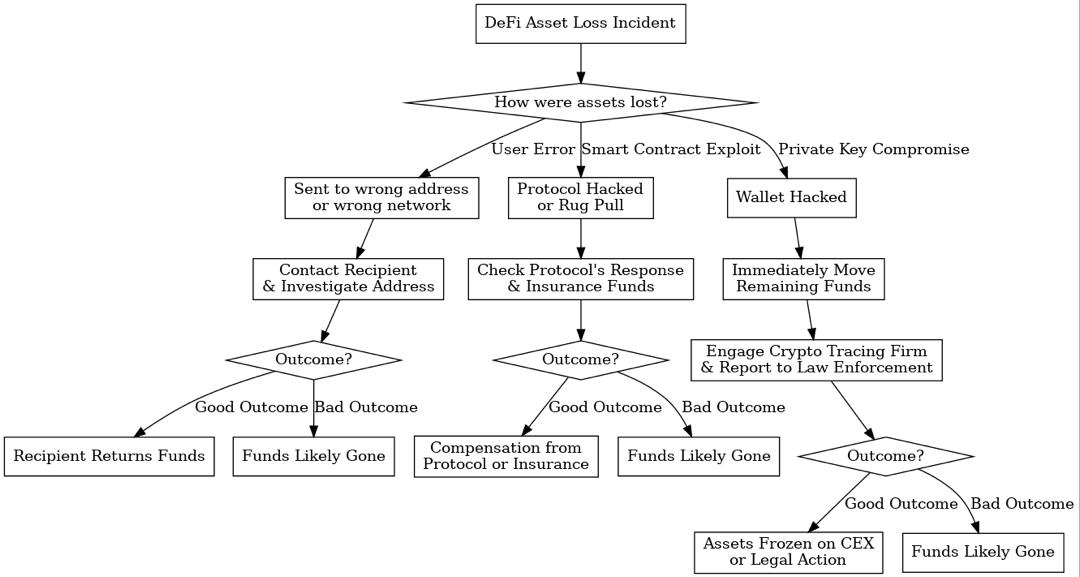
Your recovery options depend entirely on how the assets were lost. The flowchart below outlines the primary paths based on the nature of the incident.
A Realistic Framework for DeFi Recovery Attempts
While the path is difficult, a structured approach is essential.
Phase 1: Immediate Action & Diagnosis
-
Stay Calm and Verify: Confirm the loss on a blockchain explorer (Etherscan, Arbiscan, etc.). Gather the transaction hash (TXID), your wallet address, and the recipient’s address.
-
Identify the Attack Vector: Determine if it was a user error (wrong address), a approval exploit (where you granted excessive smart contract permissions), a rug pull, or a complex smart contract hack.
-
Revoke Token Approvals: If you suspect malicious contracts, use a tool like Revoke.cash or Unrekt.net to immediately revoke any permissions you’ve granted, preventing further drainage.
Phase 2: Strategic Recovery Actions
Based on your diagnosis, pursue the relevant path in the flowchart above:
-
For User Error (Wrong Address): Your only hope is that the address belongs to a reputable service or an ethical individual. Investigate the address. If it belongs to an exchange, contact their support with full details. They may assist but are not obligated.
-
For Smart Contract Exploits & Hacks:
-
Check the Protocol’s Response: Many major DeFi protocols have emergency response plans. Some maintain insurance funds (e.g., MakerDAO’s Surplus Buffer) or are covered by DeFi insurance protocols like Nexus Mutual or Insured Finance.
-
Legal Action: For large-scale, protocol-draining hacks, law enforcement agencies with cyber units (like the FBI IC3) may get involved, especially if funds are moved to a regulated CEX.
-
Phase 3: Professional Blockchain Investigation
-
Engage a Crypto Tracing Firm: For significant losses, firms like Chainalysis or CipherTrace can be hired to trace the flow of stolen funds. Their goal is to taint the assets and get them frozen when they hit a centralized exchange (CEX) that they have relationships with.
-
Report to Authorities: File a report with your local law enforcement and relevant cybercrime units. Provide them with the TXID, addresses, and any report from your tracing firm.
The Unfortunate Reality of DeFi Scams
The market is flooded with “Recovery Experts” who promise to get your funds back. 99% of these are recovery scams.
-
🚨 They contact you first via Telegram, Twitter DMs, or comments.
-
🚨 They guarantee success.
-
🚨 They demand upfront fees.
-
🚨 They ask for your private keys or seed phrase. (A legitimate service will NEVER do this).
Prevention: Your First and Best Line of Defense
In DeFi, prevention is infinitely more effective than any cure.
-
Use a Hardware Wallet: A hardware wallet is non-negotiable for serious DeFi users. It keeps your private keys offline.
-
Audit Token Approvals: Regularly review and revoke unnecessary smart contract permissions.
-
Verify All Addresses: Double-check addresses before sending. Use a browser bookmark for protocols to avoid phishing sites.
-
Start Small: When interacting with a new protocol, conduct a small test transaction first.
-
Stay Informed: Follow protocol announcements and security experts on Twitter to stay ahead of emerging threats.
DeFi Recovery Options Overview
| Method | Best For | Pros | Cons | Success Likelihood |
|---|---|---|---|---|
| Recipient Contact | Wrong address transfers | No cost; simple | Requires an honest entity | Very Low |
| Protocol Insurance | Protocol-level hacks | Potentially full recovery | Not all protocols have it | Low to Medium |
| Blockchain Tracing | Thefts & large-scale hacks | Professional, can lead to freezing | Very expensive, slow | Low |
| Legal Action | High-value thefts | Official authority backing | Extremely slow, costly, uncertain | Very Low |
Conclusion: Manage Expectations and Prioritize Security
DeFi asset recovery is an uphill battle, often with an uncertain outcome. While the pathways outlined here offer a glimpse of hope, they are fraught with challenges and are often expensive.
Your energy is best invested in robust prevention. By adopting stringent security practices—primarily the use of a hardware wallet and vigilant smart contract interaction—you can participate in the DeFi ecosystem with greater confidence and significantly reduce your risk profile. In the world of decentralized finance, you are your own bank, and therefore, your own chief security officer.

Digital Asset Recovery: A Professional Guide to Retrieving Lost or Stolen Cryptocurrency
The immutable nature of blockchain technology is a double-edged sword. While it ensures security and transparency, it also means that a single mistake—a mistyped address, a lost password, or a successful phishing attack—can lead to catastrophic, permanent loss. The growing value of the crypto space has given rise to a critical industry: digital asset recovery.
This guide provides a professional, clear-eyed overview of the recovery landscape, outlining legitimate processes, managing expectations, and providing a crucial framework for distinguishing true experts from predatory scams.
Understanding the Two Types of Recovery
Your approach depends entirely on the nature of the incident:
-
Recovery of Lost Assets: You control the keys but cannot access them.
-
Examples: Forgotten passwords, lost seed phrases, corrupted storage devices, failed transactions.
-
-
Recovery of Stolen Assets: A malicious actor has taken your funds.
-
Examples: Exchange hacks, phishing scams, ransomware, fraudulent investments (rug pulls).
-
Legitimate Avenues for Digital Asset Recovery
| Method | Best For | How It Works | Pros | Cons |
|---|---|---|---|---|
| Technical Recovery | Lost passwords, corrupted files | Uses advanced software (e.g., brute-force) to guess passwords or repair files. | Can be effective for weak passwords. | Low success rate for strong passwords; cannot help if funds are moved. |
| Blockchain Investigation & Tracing | Stolen assets | Experts use tools like Chainalysis or Elliptic to follow the fund’s path on the blockchain. | Provides crucial intelligence for law enforcement and exchanges. | Does not guarantee fund return; is a fact-finding mission. |
| Exchange Engagement | Assets sent to a CEX | Investigators work with a centralized exchange’s compliance team to freeze assets and identify the holder. | Can lead to asset freezing if acted upon quickly. | Requires a court order or strong evidence; exchange cooperation is not guaranteed. |
| Legal Action | High-value theft with an identified culprit | Lawyers file civil lawsuits or work with law enforcement for criminal charges to seize assets. | Can result in court-ordered asset restitution. | Extremely expensive, slow, and complex; requires identifying a culprit. |
The Recovery Process: A Step-by-Step Framework
-
Immediate Action:
-
Secure: If a wallet is compromised but accessible, move remaining funds to a new, secure wallet immediately.
-
Gather Evidence: Document everything: Transaction IDs (TXID), wallet addresses, screenshots of communications, and a detailed timeline. This is critical for any investigation.
-
Report: File a report with the appropriate authorities (e.g., FBI’s IC3 in the U.S., Action Fraud in the UK).
-
-
Engaging a Recovery Service:
-
Due Diligence: Research firms extensively. Look for verifiable team members, a physical address, and a history of transparency. Check reviews on the Better Business Bureau (BBB).
-
Consultation: A legitimate firm will provide a realistic assessment of your case’s viability, explain their process clearly, and be transparent about fees.
-
Contract: Understand the payment structure (e.g., retainer, contingency fee). Never agree to blanket guarantees.
-
The #1 Threat: Navigating Recovery Scams
The unfortunate reality is that the recovery industry is saturated with bad actors who target desperate victims. Extreme vigilance is required.
Red Flags of a Recovery Scam:
-
Unsolicited Contact: Legitimate firms do not find clients via Telegram, Instagram, or Twitter DMs.
-
Upfront Payment Demands: Requests for payment before any work begins are a classic scam tactic.
-
Guarantees of Success: No one can promise 100% recovery. This is an impossible claim.
-
Requests for Private Keys or Seeds: A true expert will never ask for this information. Anyone who does is trying to steal from you.
-
High-Pressure Tactics: Creating a false sense of urgency is a common manipulation strategy.
For more on this, read our detailed guide: How to Spot a Crypto Recovery Scam.
Prevention: The Ultimate Form of Recovery
The most effective recovery strategy is to never need it. Implement these professional security standards:
-
Use a Hardware Wallet: Store significant amounts on a Ledger or Trezor device. This keeps your keys offline and immune to remote attacks.
-
Safeguard Your Seed Phrase: Write it on a metal backup plate and store it in a secure location. Never digitize it.
-
Verify, Then Verify Again: Always double-check addresses before sending funds. Use copy-paste and verify the first and last characters.
-
Enable Advanced Security: Use authenticator app 2FA, not SMS. Use strong, unique passwords managed by a password manager.
For a deeper dive on security, see our article: The Professional’s Guide to Hardware Wallet Protection.
Conclusion: A Realistic Outlook
Digital asset recovery is a challenging, often uncertain field. While legitimate services exist that combine blockchain forensics with legal action, they are typically costly and focused on high-value cases. Success is never guaranteed.
Your strategy should be twofold:
-
Practice impeccable security hygiene to minimize your risk.
-
If an incident occurs, act swiftly, document everything, and engage only with thoroughly vetted, transparent professionals.
Digital Asset Recovery The NFT Recovery Process: A Step-by-Step Guide
Step 1: Immediate Action and Diagnosis
-
Stay Calm and Verify: Immediately check the transaction on a blockchain explorer like Etherscan or Polygonscan. Confirm the NFT was transferred and note the recipient’s wallet address.
-
Secure Remaining Assets: If your wallet is compromised, immediately transfer any remaining assets to a new, secure wallet with a newly generated seed phrase. Do not use the compromised wallet further.
Step 2: Reporting the Theft
-
Report to Law Enforcement: File a report with your local police and relevant cybercrime units (e.g., the FBI’s IC3 in the U.S.). While they may not be able to recover the assets directly, an official report is crucial for further action and insurance purposes.
-
Report to the NFT Project Community: Alert the project’s official Discord, Twitter, and moderators. Reputable projects can flag the stolen NFT on marketplaces, making it harder for the thief to sell it. Provide the transaction hash and details.
Step 3: Engaging with Marketplaces
-
Contact Marketplace Support: Reach out to the support teams of major marketplaces like OpenSea, Blur, or LooksRare. They can sometimes:
-
Delist or Flag the Asset: They may hide the NFT from their marketplace or mark it as suspicious, protecting potential buyers.
-
Provide Information: They can assist investigations, though they will not reverse transactions.
-
Step 4: The Role of Blockchain Analysis
-
Hire a Crypto Investigation Firm: Specialized firms like Chainalysis, TRM Labs, or CipherBlade can trace the movement of stolen NFTs. If the assets are moved to a regulated exchange, these firms can work with the exchange to freeze the account and identify the holder, potentially leading to recovery through legal channels.
The Hard Reality: Limitations and Scams
It is vital to understand what is not possible and to guard against secondary scams.
-
Transactions are Irreversible: No one can reverse a confirmed blockchain transaction. This is a core feature of the technology.
-
No Central Authority: There is no “customer support” for the Ethereum blockchain to cancel a transaction.
-
Beware of Recovery Scams: In the wake of a theft, you will be targeted by “recovery experts” on Twitter and Telegram. They are all scams.
-
🚩 Red Flags: They contact you first, demand upfront fees, guarantee recovery, or ask for your private keys or seed phrase.
-
Comparison of NFT Recovery Avenues
Method Best For How It Works Pros Cons Marketplace Reporting All stolen NFTs Requesting platforms to delist or flag the asset. Prevents scam sales; raises awareness. Does not return the NFT; effectiveness varies. Blockchain Analysis High-value thefts Tracing asset flow to off-ramps like exchanges. Can lead to identity discovery & legal action. Expensive; not guaranteed; for large cases only. Legal Action Thefts with an identified thief Filing a civil lawsuit or criminal complaint. Official channel for asset seizure. Extremely costly, slow, and requires evidence. Community Support Projects with strong Discord Alerting mods to warn others and track the thief. Fast, community-driven protection. Does not recover the asset.
Prevention: The Only True “Recovery” Strategy
The most effective way to recover an NFT is to never lose it. Implement robust security practices:
-
Use a Hardware Wallet: Store your NFTs in a wallet like Ledger or Trezor. This keeps your private keys offline and isolated from internet-based attacks.
-
Guard Your Seed Phrase: Never digitize it. Write it on metal and store it securely. Never share it.
-
Be Wary of Smart Contracts: Never sign a smart contract you don’t understand. Use revoke.cash periodically to revoke token allowances.
-
Verify URLs and DMs: Always navigate to websites directly. Do not click links in Discord DMs or emails, as they are often phishing attempts.
Conclusion: Manage Expectations and Prioritize Security
NFT recovery is an arduous, often uncertain process that is rarely successful for the average user. The decentralized nature of blockchain means the responsibility for security lies primarily with the holder.
Your best course of action is a swift, methodical response: report the theft, alert the community, and engage professionals for high-value cases. However, your primary focus must be on prevention. By adopting cold storage and practicing impeccable digital hygiene, you can protect your digital collection and avoid the need for recovery altogether.
NFT Recovery -